Embracing Open Source for Advanced Endpoint Detection and Response: A Comprehensive EDR Solution…
Traditional commercial Endpoint Detection and Response (EDR) solutions, while effective, often come with prohibitive costs and inflexible frameworks that may not cater to all organizational needs. This has led to an increasing shift towards innovative, homegrown cybersecurity solutions by many hobbyists and commercial users alike.
A prime example of this shift in my life is my development of an attempt at an EDR system using Wazuh, TheHive, and MISP, integrated into a cohesive framework that leverages the power of open-source technology. This solution, engineered from the ground up, not only challenged me, but in fact proposes a question on the efficacy of commercial products against solutions that are capable of doing the same but do so at a fraction of the cost, while offering heightened flexibility and adaptability.
Introduction to the Integrated EDR Solution
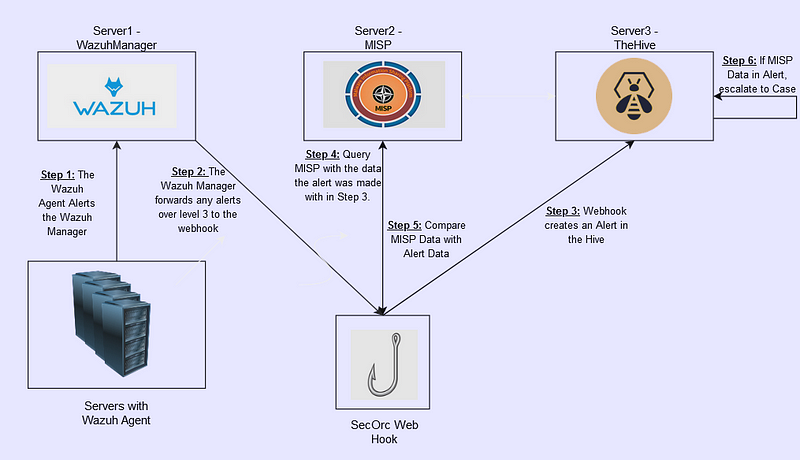
This paper explores an approach to substituting EDR, wherein key open-source tools — Wazuh for monitoring and alerting, TheHive for incident response, and MISP for threat intelligence — are seamlessly integrated. This integration is enhanced by the automation capabilities of ThreatIngestor, an opensource tool designed to enrich the threat intelligence process by automating the ingestion of indicators of compromise (IOCs) from a variety of sources like Twitter, Blogs, RSS feeds, etc.
In-Depth Explanation of the Homebrew EDR Solution Using Wazuh, TheHive, and MISP
The proposed cybersecurity solution integrates three key open-source tools — Wazuh, TheHive, and MISP — into a cohesive system designed to detect, manage, and respond to security incidents. This section delves into the specifics of how these components are configured and work together to provide a robust endpoint detection and response platform.
1. Project Structure and Setup (https://github.com/NovokumPescitarum/SecOrc)
The project comprises several Python files each serving a distinct role:
- config.py: This module handles the configuration of the environment. It reads from environment variables set in a
.envfile, which includes the API URLs and keys for TheHive and MISP, as well as SSL certification settings for MISP. - main.py: Sets up and runs the Flask application, which listens for incoming HTTP requests. It also configures basic logging and disables SSL warnings to streamline the output.
- routes.py: Defines the Flask routes that handle incoming webhook requests. It processes JSON data received from Wazuh and passes it to TheHive for alert creation.
- misp.py and thehive.py: These modules interact with the MISP and TheHive APIs, respectively. They include functions to search for hash matches in MISP and to create alerts and cases in TheHive based on the findings.
- utils.py: Provides utility functions for extracting data from JSON payloads and parsing hash data, facilitating data manipulation and preparation for API interactions.
2. Webhook Reception and Data Processing
The system is designed to receive JSON data via a webhook, typically sent by Wazuh when it detects a potential threat. The routes.py file defines an endpoint that accepts these POST requests. Upon receiving a request, the JSON data is extracted and transformed into a flat dictionary using recursive functions defined in utils.py. This data is then used to generate a unique alert ID if not already provided.
3. Alert Management with TheHive
After preprocessing the data, thehive.py is invoked to construct an alert object using data such as the severity of the alert and various fields extracted from the JSON. TheHive API is then used to create an alert in the TheHive system. The alert includes details such as hostname, source and destination IPs, and other pertinent information. Each alert can have artifacts associated with it, which are also generated based on the extracted data, excluding specific keys that are not relevant to the artifacts.
4. Threat Intelligence with MISP
Concurrently, the misp.py module uses the hash values extracted from the alert data to search for matches in MISP. This is crucial for identifying if the hashes related to the alert have been observed in other incidents or are known to be associated with malicious activities. The search results can trigger additional actions, such as the creation of a detailed case in TheHive, should any matches be found.
5. Case Creation in TheHive
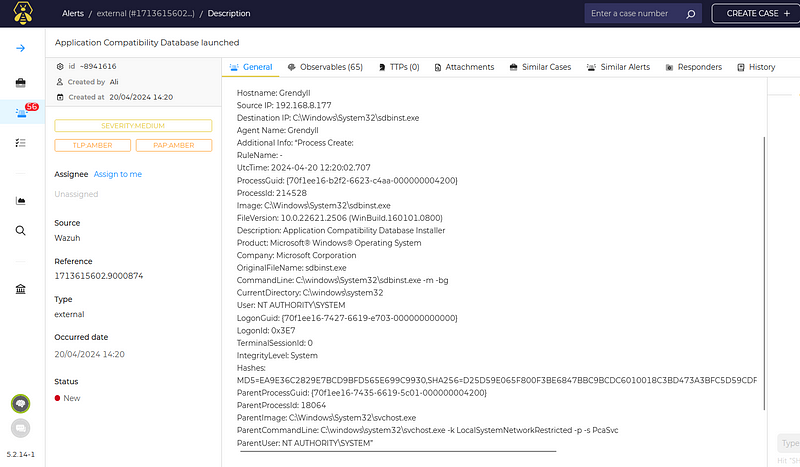
If hashes from the alert are found in MISP, thehive.py proceeds to create a detailed case based on the alert. This case includes comprehensive descriptions and all the observables associated with the alert, enhancing the investigation capabilities within TheHive. Each case also tags and categorizes the incident for easy tracking and reference.
Enhancing MISP with ThreatIngestor
A key enhancement in the threat intelligence capability of this solution is the integration of ThreatIngestor. This tool is configured to automatically monitor and extract IOCs from configured sources, significantly expanding MISP’s utility by keeping its threat data current and comprehensive. This integration not only automates a crucial aspect of threat intelligence but also ensures that the data is relevant, timely, and actionable.
Wazuh Configuration for Webhook Notifications
Critical to the operation of this EDR solution is the configuration of Wazuh to send webhook notifications. This is accomplished by modifying the ossec.conf file to include a custom webhook integration that directs alerts to the Flask application. The configuration specifics ensure that alerts of a certain severity are pushed to the system, where they are immediately processed, showcasing the system's capability to handle real-time threat data efficiently.
<integration>
<name>custom-webhook</name>
<hook_url>http://<your_flask_server_ip>:<port>/webhook</hook_url>
<alert_format>json</alert_format>
<level>3</level>
</integration>
This setup not only exemplifies the integration of Wazuh within the broader EDR framework but also highlights the system’s flexibility in configuring operational parameters to match specific security policies.
Operational Flow and Data Processing
The operational flow of the system begins when Wazuh detects an event that triggers an alert. This alert is formatted as a JSON object and sent to the Flask application via the configured webhook. Upon receipt, the JSON data is parsed and processed to extract relevant information, which is then used to create detailed alerts and cases within TheHive. Concurrently, hash values extracted from the alert are used to search for related IOCs in MISP, further enriching the context of the incident being managed.
Choosing Direct API Integration Over Automation Frameworks Like Shuffle
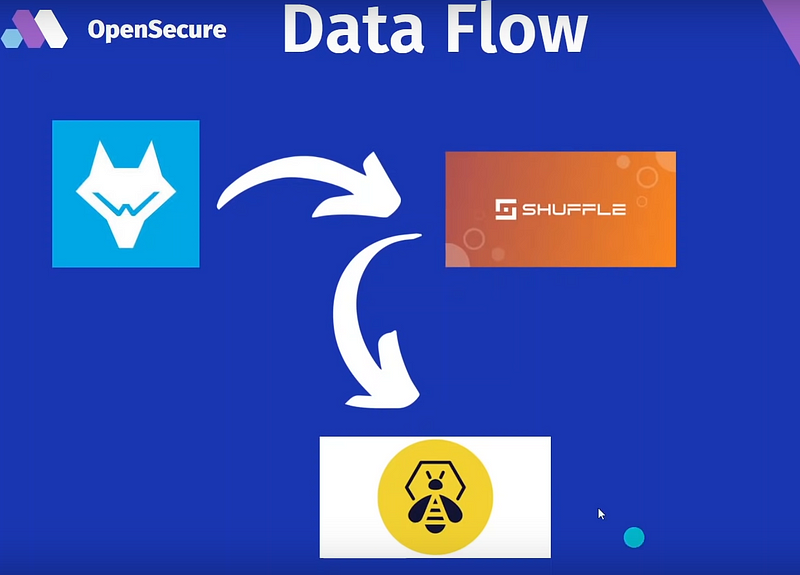
In the development of this comprehensive EDR solution, a deliberate decision was made to utilize direct API programming rather than adopting popular automation frameworks such as Shuffle, which is what is currently recommended (YouTube). This choice stemmed from a detailed evaluation of the operational requirements and the need for a high-performance, adaptable system.
Rationale Behind the Decision
- Performance Considerations: Automation frameworks like Shuffle, while powerful and user-friendly, introduce a level of abstraction and overhead that can impact the system’s performance. During preliminary testing and research, it became evident that the additional overhead from these frameworks could slow down the data processing speeds. For an EDR system, where real-time response and alert processing are critical, even slight delays introduced by such frameworks could hinder operational efficiency.
- Complexity and Overhead: Shuffle and similar tools are designed to simplify workflow creation through graphical interfaces and pre-built integrations. However, this simplicity often comes at the cost of increased computational overhead and less control over fine-tuning performance aspects. In high-stakes environments where every millisecond counts, maintaining direct control over the processing and data flow is paramount.
- Learning Curve and Flexibility: Utilizing direct API interactions allows for more granular control and customization, leveraging existing programming skills without the need to learn new platforms or languages. This approach not only reduces the time spent on training and adaptation but also enhances the system’s flexibility, enabling quick adjustments and custom integrations that are not always feasible with more rigid framework structures.
- Tailored Integration: The chosen approach of direct API programming aligns with the need for a highly customized solution that integrates Wazuh, TheHive, and MISP in a specific, optimized manner. This customization ensures that the system is not only robust and secure but also perfectly tailored to the specific operational needs and threat landscapes of the organization.
Future Integration Plans
Looking ahead, SecOrc plans to integrate additional tools to broaden its detection and response capabilities:
- Velociraptor: An advanced monitoring tool that performs live forensic data collection across endpoints. Integrating Velociraptor will enhance the project’s ability to perform detailed investigations and real-time monitoring.
- YARA: A tool for identifying and classifying malware based on custom rules. Its inclusion will improve the system’s capability to detect sophisticated threats through pattern matching.
- ClamAV: An open-source antivirus engine that can detect trojans, viruses, malware, and other malicious threats. It will add an essential layer of virus scanning to the orchestrated response.
Conclusion
In this paper, I have detailed the architecture and implementation of an integrated Endpoint Detection and Response (EDR) system utilizing Wazuh, TheHive, and MISP — three formidable open-source tools. This solution aims to offer a flexible, cost-effective alternative to traditional commercial EDR systems, with a strong emphasis on adaptability and customization through direct API integration and a user-centric operational model. However, it’s crucial to note that this system is still in the experimental phase.
The actual efficacy and performance of this open-source EDR solution, compared to its commercial counterparts, have yet to be fully tested. Key aspects such as scalability, security, user-friendliness, and compliance with legal standards require extensive validation across various real-world scenarios. Moreover, my future plans for integrating tools like Velociraptor, YARA, and ClamAV are designed to enhance the solution’s capabilities and will also need rigorous evaluation to determine their impact on the overall system performance and reliability.
Going forward, my focus will be on conducting comprehensive testing and collecting detailed feedback from initial deployments. This will involve stress-testing the system under diverse network conditions, benchmarking its performance against leading commercial solutions, and refining its functionality based on user feedback and the evolving landscape of cybersecurity threats. By undertaking these steps, I aim not only to validate but also to refine my solution to ensure that it meets the rigorous demands of modern cybersecurity environments and proves itself as a viable alternative to commercial EDR systems. The journey towards a fully validated open-source EDR solution is both challenging and exciting, and I am committed to advancing this project to potentially set a new standard in the cybersecurity field.