How I Hacked Free IPTV (And Stumbled Into a Data Leak Goldmine)
This story is shared for educational purposes only. No systems were harmed, no services were disrupted, and the affected provider has been informed responsibly. The aim is to raise awareness on insecure API implementations and data leakage.
Intro
I’ve been considering this notion that I believe all developers, hackers and other tech-magicians should also consider. I dared myself to program or hack something that even my mom would find useful. To wit, I ended up with the idea that for all my knowledge, I should at least be able to get some free television. That journey was interesting and perhaps a little unsettling.

The Target: IPTV Provider With a Weak Login Flow
I started by casually Googling around, curious to see how many small-scale IPTV providers might be running insecure systems. After a few minutes of digging through forums and trying out combinations like site:*.com inurl:login and IPTV trial, I landed on a provider offering email-only authentication for registered users.
No password. No 2FA. Just an email.
⚠️ Red Flag #1: Email-only authentication is like leaving your door open and asking visitors to knock politely before walking in.

Recon: Peeling Back the Portal
Once inside the login page, I opened DevTools and saw a few AJAX calls flying to a familiar-looking endpoint:
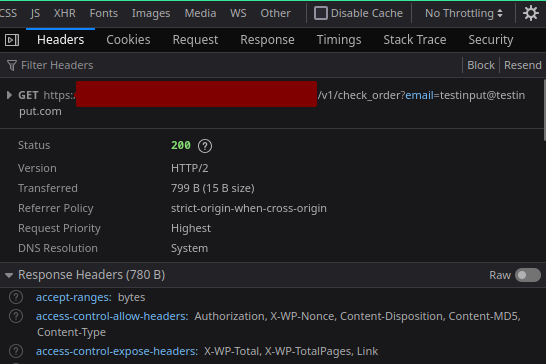
WordPress. Classic.
I confirmed the server was running WordPress by checking for:
/wp-json/v1/
The presence of /wp-json/v1/ hinted that the site was using a custom REST API, possibly built with a WordPress plugin or theme backend.
API Fiddling: Enumerating the Hidden Endpoints
Using the chrome DevTools I watched some network packets and:
I discovered two juicy endpoints:
GET /wp-json/v1/get_orders— required an email for authorization
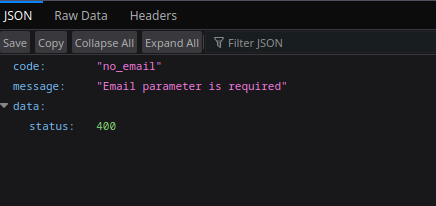
GET /wp-json/v1/get_processing_orders— did not require authentication
Here’s a redacted request/response that made my jaw drop:
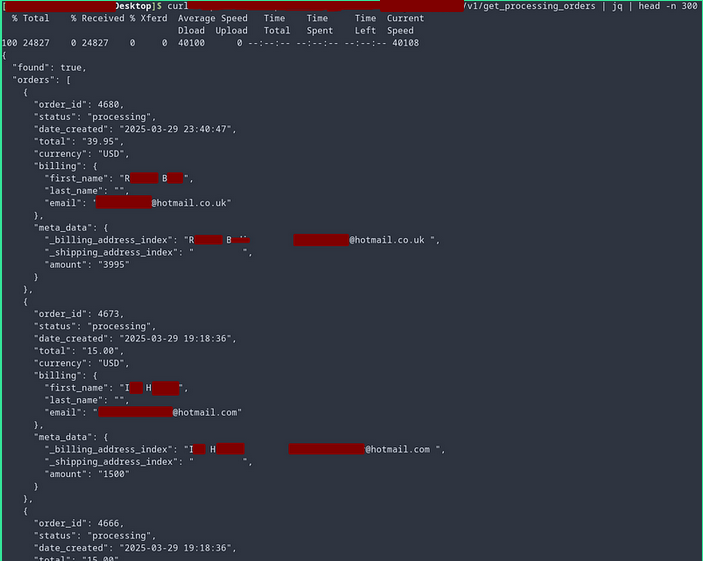
⚠️ Red Flag #2: This API endpoint exposed personally identifiable information (PII) with zero authentication.
To be clear, IPTV is a criminal enterprise, and people who use it can be considered as committing a crime. This provider’s bad security practices are not only putting their service in danger, it’s putting their clients in danger as well.
Exploitation: From Leaky Orders to Free Streams
From here, the rest was trivial:
- I pulled the list of email addresses and M3U URLs.
- Tried logging in with just the email (no password required).
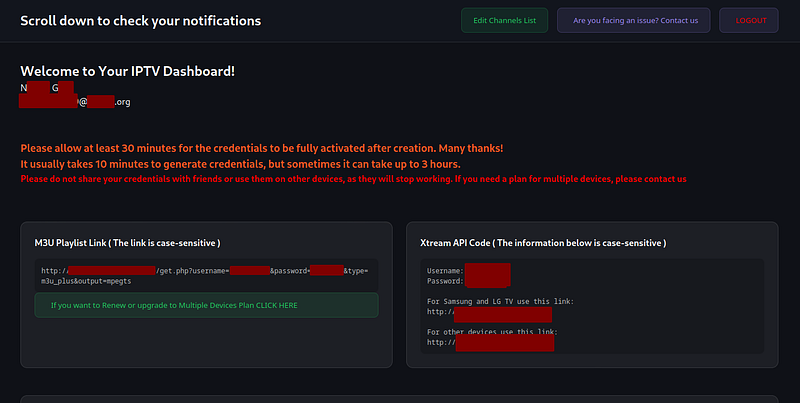
3. Success. I now had full access to the IPTV dashboard.
3. I downloaded the M3U playlist and loaded it into my Media Center.
I was now watching live TV and VoD (Movies and Series) — for free.
🎥 Live sports, premium movie channels, adult content — all behind an API that a toddler could poke.
Beyond Free TV: A Privacy Nightmare
This wasn’t just about watching free streams. The data exposed by the endpoint included:
- Full names
- Emails
- Billing addresses (sometimes)
- Subscription details
📛 I had full visibility into hundreds of users’ private info in a criminal enterprise.
This was no longer just a fun CTF-style hack. This was a massive arrest raid just waiting to happen… What would you do in this kind of situation?
Does it make sense to help a criminal group if it means it helps helping their customers who are arguably not committing such a terrible crime that it warrants their privacy to be entirely compromised?